You may not hear about social engineering attack in your daily life, but it is very common. This article on MiniTool Website will answer this question. Social engineering is so rampant that you can get attacked at any time by an accidental click. You can’t be too careful about that.
What Is Social Engineering Attack?
It is universally acknowledged that personal information is more and more important in daily life. However, with the development of science and technology, you are confronted with the risks of divulging your crucial data.
Social engineering is a kind of artifice which is employed by criminals to gain your sensitive information or access to your accounts. The attackers make use of social communication skills to ask you some questions without your knowledge. To get your trust, they may pretend to be some new staffs, maintenance workers, toll collectors and so on.
Types of Social Engineering Attacks
There are 5 types of social engineering attacks in total. We’ll introduce them one by one in the following pages.
Scareware
Scareware is also called ransomware or deception software. It pretends to be legal by sending you warnings that claim your device or your files have been infected thus providing a fake antivirus software for you to download.
At the same time, it also distributes some bogus warming to induce you to download or pay for some useless and harmful services. All their attempts are to invade your PC and steal your personal data.
Pretexting
Pretexting is also a type of social engineering for culprits to cheat your trust. In this type of social engineering, the frauds usually impersonate a trusted individual and tell you that they need details to confirm your identity. As soon as you comply, they will use your data to execute other criminal activities.
Baiting
As its name suggests, baiting is to give you something as baits to appeal to you. Attackers take advantage of the curiosity and greed of human nature to put in their login credentials. Therefore, don’t download any free music or movie via strange websites.
Quid Pro Quo
Quid Pro Quo is a kind of social engineering which is similar to baiting. The difference is that Quid Pro Quo takes the form of service while baiting assumes the form of a good. They may claim that they are the staffs of some authoritative organizations such as Social Security Administration. Fraudsters steal your identity information by setting up a fake website that looks like a reliable one.
Phishing
Is phishing a social engineering attack? Of course, it is! Phishing is the most common type of social engineering. Attackers may have known some of your privacy such as your name, phone number, e-mail number, workplace, etc.
They may send you a message or email to announce to you that your password on a certain website is about to expire hence seducing you to type your username, password and other personal data to verify your identity in a given link. Be Careful of YouTube Email! It Might Be the Phishing Scam takes YouTube email as an example to show the danger of suspicious emails.
How Can You Protect Yourself from Social Engineering Attack?
After knowing what social engineering attack is, you must be curious about how to protect yourself from it. Enterprises and users are supposed to pay attention to being attacked by social engineering.
Usually, the tricks include spelling mistakes or changed domain names thus they are frauds. To avoid getting hooked, you had better try the next methods.
Method 1: Use Two-factor Authentication
2FA is always considered a good way to counter the attacks of social engineering. It adds an extra verification layer when you log in certain programs. To access these programs, you must verify some questions besides typing your user name and password.
Method 2: Think Before You Click
There is no such a thing as a free lunch. As a result, any messages like a lottery or money from unknown relatives, or a request to refund from a foreign country must be a scam. Refuse to click untrusted links because legal firms and associations don’t need to contact you for help. Pay attention to those suggestions like helping to restore your credits scores.
Method 3: Set Spam Filters to High
Just find your setting options in email and set your spam filter to high. Most malicious emails can be stopped by this feature. All you need to do is to check your spam folder at a regular time to see whether any legitimate email has been trapped there by accident.
Method 4: Change Your Password at Times
Don’t use the same set of passwords and user names on every software or else as soon as attacked by others, all your application data is given away. The criminals are so tricky that they will try the same credentials on your other accounts. If sometimes you have to log in your account on a strange device, you had better change your password after that since you have a risk of losing your account.
Method 5: Conduct Relevant Security and Training
To avoid being attacked by such social engineering, communities should organize some universal user network security training. Conducting simulations is a good way to immerse users in a real case of social engineering attacks thus they can know the attacks better in practice.
What to Do If Encountering Social Engineering?
Fix 1: Change Your Account Password
Changing all your account passwords is the most recommended. What’s more, you should block your bank account at once because the attackers may draw out your money as soon as they gain your data. Email passwords are the most important and they must be complex enough to meet the standards of email password policies.
Fix 2: Make Use of Law Enforcement
If the loss is severe, you had better file a report to the relevant regulatory authorities and law enforcement. The countermeasure and judicial action depend on the extent of the damage that the social engineering accidents have caused.
Fix 3: Report the Attack
The targets of attackers are usually so extensive that they aim at a large scale at a time. They tend to attack the people in the same organization. Reporting social engineering accidents in time can increase the awareness of other people hence avoiding more unexpected data or money loss.
Fix 4: Search Internal Systems
Searching your DHCP logs and firewall logs to see if there are suspicious IPs or URLs and if your traffic is flowing to those addresses. Some smart attacks will change their IPs every few minutes, so you need to check your DNS logs to examine whether your computer is looking for them.
Although we have shown you helpful solutions to protect yourself from social engineering attacks and effective ways to solve this tricky problem when suffering from it, the social engineering attack is so rampant that no one can immune from it. In the final analysis, it is the data security that matters most in today’s information age.
Therefore, here comes the question – how to keep your data safe and be a “lucky” victim? In the last part of this article, we will focus on this issue and you must make sure to follow each of them diligently for the best expedients.
How to Keep Your Data Safe?
Way 1: Backup Your Files with MiniTool ShadowMaker
When it comes to data protection, nothing matches a professional backup software, MiniTool ShadowMaker. It is freeware that can be used to back up data in files & folders and partitions & disks. What’s more, it is a user-friendly software since it can protect the security of important data to avoid any accidental data loss. For a safe and free backup and data protection service, you can try to download MiniTool ShadowMaker Trial which you can use for free within 30 days.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Without further ado, let’s start to see how to backup data step by step.
Step 1. Download and install this free file backup software and run it. Click on Keep Trial to begin the journey of backup.
Step 2. Click Backup to open the backup feature.
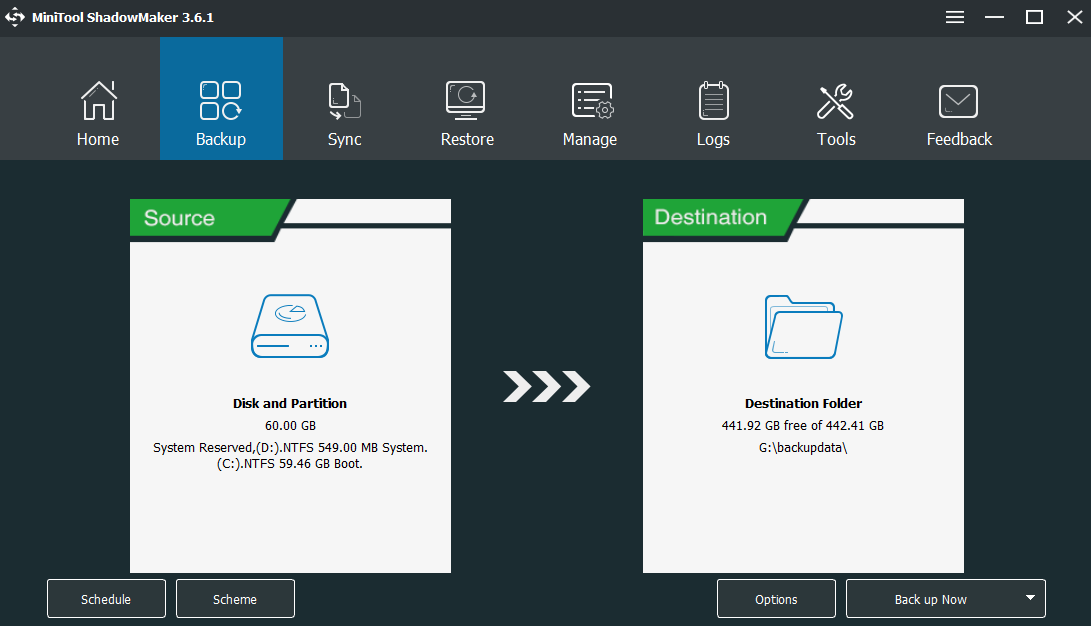
Step 3. Hit Source on the left and choose Folders and Files in the popping-up window.
Step 4. View the source and choose the desired files or folders you want to back up and tap on OK.
Step 5. Return to the main interface of Backup, click Destination to choose a destination path.
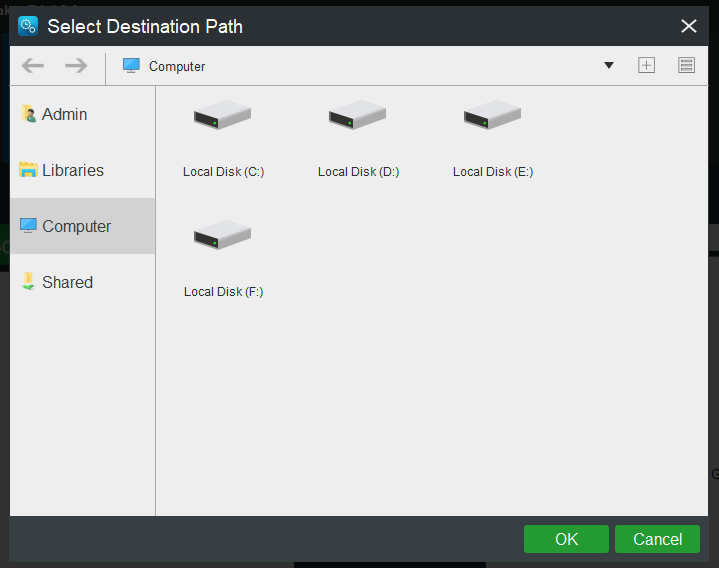
Step 6. After selecting the desired location, click OK.
Step 7. Click Back up Now or Back up Later. File backup won’t take you much time, so you can execute the backup task immediately by clicking the former one. The backup result will be shown in Manage.
Way 2: Protect Your Data with MiniTool Power Data Recovery
Of course, there’s another professional data recovery software for you, MiniTool Power Data Recovery. In order to resist the attack of social engineering, you should make full preparations for urgent situations. When the attackers do something harmful to your drives, you can still quickly find and recover files with this powerful data recovery assistant.
MiniTool Power Data Recovery TrialClick to Download100%Clean & Safe
Step 1. Download and install MiniTool Power Data Recovery Trial and open it.
Step 2. Choose the inaccessible or damaged drive that was destroyed by attackers to scan.
Step 3. After the scanning is done, you can see all partitions of this drive and a folder named More Lost Files. Click them one by one to browse their contents and you can check the ones you needed to save them to another normal drive. It is highly recommended to recover data from the More Lost Files folder. Click the wanted ones and save them to another drive.
Look for a more detailed tutorial, please go to – How To Recover Data From Corrupted Internal Hard Drive | Guide
Final Words
How can you protect yourself from social engineering attack? What is the most effective way to detect and stop social engineering attacks? I believe your answer is very clear now. To know more hot IT information or services about data protection, please feel free to contact us via [email protected]!

