What Does a Hacker Do?
As cyber activities are rising and becoming the main enthusiasm in leisure time, some with bad intentions find their way breaking people’s protection shield and developing into various types of hackers. They hide in the dark, lock their attacking targets, and easily infiltrate victims’ systems.
Sometimes, if the hacker applies hacking methods in a more flexible and sophisticated way, it will take a longer time to crack, and even never be able to decode the technique. So, the danger persists.
Hackers are rising. They normally have been equipped with well-trained brains and skills. With different purposes and practical experience, they can flexibly deal with all kinds of emergencies, luring victims to leave a security hole for the next infection.
Hackers can do many things as long as they infiltrate your system, such as:
- Install malware
- Steal or destroy data
- Disrupt services
- Gather information from users
- …
Now, according to the purposes and hacking techniques, we can categorize some major hacker types. For specific information about different types of hackers, please keep reading.
Types of Hackers
White Hat Hackers
Are all hackers bad? No, since some high-skilled people join the hacking group, more and more professionals are rising to the occasion and exploring their hacking techniques via simulated attacks. We call them ethical security hackers or white hat hackers.
They will mimic all the possible hacking techniques to identify security vulnerabilities that the current system has. By doing so, people can take prompt measures to enhance the security weakness. Different from other hackers, white hat hackers often adhere to a well-developed moral compass and law-based regulations.
Black Hat Hackers
Black hat hackers initiate activities that are totally against laws or ethical standards for nefarious purposes. They can make use of malware, ransomware, viruses, and other tactics to disrupt a system’s defense. Then, those criminal hackers will hold computers hostage, or steal usernames and passwords, credit card numbers, and other confidential info.
The most common hacking techniques they will use include phishing, Trojan Horse, spyware, adware, brute force, identity theft, ransomware, man-in-the-middle, logic bombs, clickjacking, denial-of-service, and so on.
If you wonder about more information about white hat hackers and black hat hackers, you can read this article: [Explained] White Hat vs Black Hat – What’s the Difference.
Gray Hat Hackers
Gray hat hackers are somewhere in between these two meanings – white hat hackers and black hat hackers. They may play as computer hackers or security experts to execute a series of hacking activities. Those moves, sometimes, may violate laws or ethical standards but should not be identified as malicious.
The hackers normally operate in the nebulous area and don’t have malicious intent typical of a black hat hacker.
Red Hat Hackers
Apart from the above types of hacker hats, red hat hackers are a group of vigilante hackers. They hold disparate intentions in a state of opposition. Red hat hackers tend to use their knowledge and tactics to battle against cyber criminals and cyberwarfare that do not meet their own moral values or high standards of justice.
What red hat hackers do may be illegal because sometimes, they may apply aggressive steps to hold back black hat hackers. Everything they do is not simply for cyber security, but to meet a desire to fight back against black hat hackers.
Green Hat Hackers
Another type of hacker hat is green hat hackers. Green hat hackers are a bunch of novices or beginners who seek a way to learn more about cybersecurity and train their skills. So, in their hackings, many mistakes will happen and even cause irreversible damage by accident.
Some of them may start the business and pave the way to becoming an excellent white hat hacker but some may hold malicious intentions.
Blue Hat Hackers
Blue hat hackers are a group of cybersecurity experts involved in organizations that require higher protection to cope with potential threats. These kinds of hackers normally have professional backgrounds and are invited to join corporations or organizations.
They will perform penetration testing and sniff out bugs and vulnerabilities for enhancement before the product is released to the market. This appellation is not widely recognized so, many people will confuse them with white hat hackers.
Gaming Hackers
As the name implies, gaming hackers refer to those individuals who focus on stealing credit caches from professional gamers or their competitors. Those hackers can also perform distributed denial-of-service (DDoS) attacks to force their competitors out of the game.
Once, more than four million such attacks were launched targeting the global gaming community. With the high value of the video game industry, many hackers have shifted their focus to this field.
Script Kiddies
Script kiddies, in a derogatory sense, refer to those novice hackers with little skilled experience and related knowledge. Hackers often use this name with contempt because they use hacking tools with little understanding.
Script kiddies are often ignored but they are dangerous with bad intentions to compromise other people’s computer systems.
Hacktivists
Hacktivists are more serious than other types of hacker attacks. They start the attack not for the lure of money but for political or social causes. The participants will leverage digital techniques to present their discontent and resistance. In this way, they can put a spotlight on a social or political event.
Government departments and organizations are the main targets for those hackers, not just attacking them but defacing them. It is hard to judge their positions. They may work for hostile organizations or work to promote issues related to freedom of speech, human rights, or information ethics.
Cryptojackers
Cryptojackers refer to hackers who exploit a computer to mine cryptocurrency via the unauthorized use of someone else’s computing resources. They often infiltrate one’s computer by seducing victims to unwittingly install a program with malicious scripts.
State-Sponsored Hackers
Those hackers are supported and sponsored by states and can develop more high-tech skills and explore more advanced attack vectors. They often work for a nation’s interest at home or abroad and are driven by political, military, or economic factors.
Under the background of national strength, they can access a wealth of resources they need and build up formidable capabilities. They are regarded as one of the most dangerous types of threat actors.
Elite Hackers
Elite hackers are regarded as the top tier with years of hacking experience behind their skills and expertise. They can be the best of the best when it comes to hacking, invent new ways to start attacks, and find and exploit vulnerabilities before anyone else does.
They are often associated with black hat activities but sometimes, they will act as white hat hackers to promote cyber security.
Whistleblowers
Whistleblowers, or malicious insiders, are persons/employees, who expose information to the public and the information is deemed illegal, immoral, illicit, unsafe, or fraudulent.
In computing, whistleblowers are guys who steal private data to draw attention or cause damage to the organization they work for. We judge them for who they are according to what they expose.
Cyberterrorists
Cyberterrorists refer to a more extensive definition including cyber-attacks that intimidate or generate fear in the target population. What they perform can be a personally- or politically-motivated attack and that will cause threats on a country’s critical infrastructure or networks.
Different organizations have varied definitions of cyberterrorism. For example, some organizations think the cyber activities that have threatened people’s lives can be called cyberterrorism.
Those cyberterrorists, mostly, apply politically motivated illegal attacks against systems, information, programs, and data and agitate violence against noncombatant targets. Those targets can include the banking industry, military installations, power plants, air traffic control centers, water systems, etc.
Botnet Hackers
Botnets are built to grow, propagate, and automate to assist large attacks. Sometimes, botnets seem to be good ones to help carry out complex computational processes but malicious botnets are utilized to send spam or steal user data.
A botnet is a network of computers used to perform several routine tasks and each individual device that is being controlled is called a zombie PC. The hackers can drive the actions of those zombie bots from remote and the infected devices can level up to hundreds, thousands, or even millions at once.
That’s why botnet hackers can carry out high-volume attacks, jeopardizing a large number of network systems.
How to Protect Yourself from Hackers?
Faced with so many threats, we need to take some measures to better protect ourselves from hackers.
1. Use antivirus and firewall to perform real-time protection.
2. Perform regular updates for your system and other devices.
3. Use dual-factor authentication as an extra layer of security for your online data.
4. Don’t access important data related to privacy or financial information via public Wi-Fi.
5. Disable some useless connections, such as GPS, wireless connection, Bluetooth, or geo-tracking.
6. Think twice before you install an app, especially those with an unknown source. If you can’t be certain of its authenticity, just don’t install it.
7. Keep skeptical of any links and attachments.
8. Use a strong password and encrypt the private data on your device.
9. Be aware of email messages from unknown parties and some phishing emails may mimic someone you know. You should keep your eyes open for the suspicious contents.
10. Back up your data or system; rebuild it when necessary.
Backup Expert – MiniTool ShadowMaker
We are under the cyber threat and remedial measures should be prepared for accidents. Then, we recommend data backup as your last resort to minimize your loss. It can help recover backed-up data when you run into all kinds of problems, such as system crashes/errors or drive/file corruption.
MiniTool ShadowMaker is a free backup software used to quickly back up files & folders, systems, hard drives, and partitions. You can prepare an external hard drive for data backup, which can directly avoid hacking.
MiniTool offers a series of trustworthy functions, such as:
- Reliable backup solutions
- Quick system restores
- Automatic file sync
- Safe disk clone
- Flexible backup schedule
- Smart backup management
Download and install this program and you can get a 30-day free trial version. If you want to back up data to an external hard drive, please insert it before you launch the program so that the drive can be recognized.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
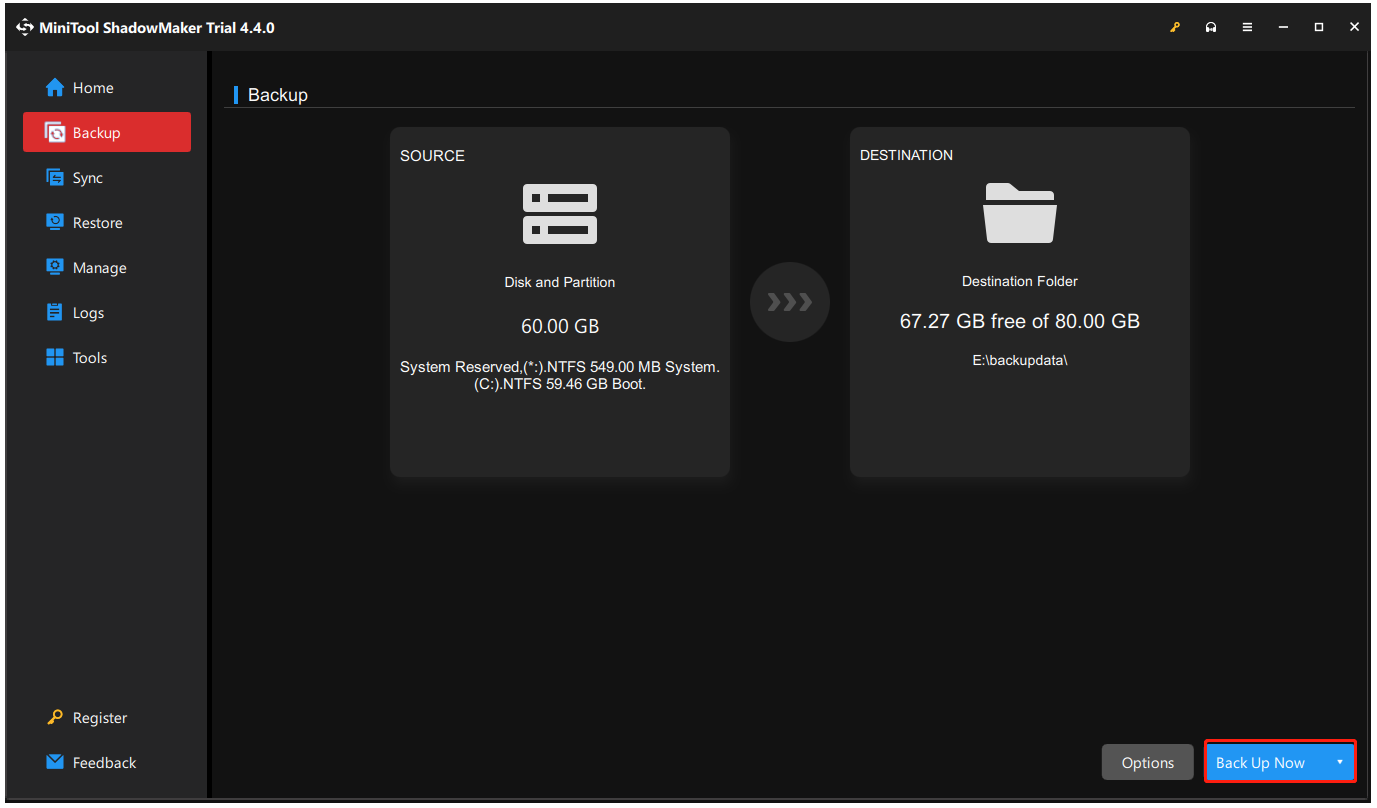
Step 1: Double-click on the program and click Keep Trial to enter the interface.
Step 2: In the Backup tab, choose the SOURCE section to choose what you want to back up, and then go to the DESTINATION section to choose where to save backup.
Step 3: Then you can click Options to configure the backup settings, such as Image creation mode, File size, Compression, etc., and click Back Up Now to start the task immediately.
MiniTool has another feature that allows users to create bootable rescue media in this way your system can get restored when the computer fails to boot. In case of severe issues caused by hackers, you’d better try this one.
In addition, with the help of MiniTool ShadowMaker, you can add a boot menu, encrypt backup images, and back up a remote computer. It is worth trying to keep your PC protected with a higher level of data security.
Bottom Line:
This article has introduced all the common types of hackers. They have different purposes and apply varied techniques for the infection. Faced with such cunning enemies, you need to raise the consciousness of cyber security and follow the tricks we provide in the above content to protect yourself from hackers.
If you have any problem when using MiniTool ShadowMaker, you can contact us via [email protected] and we have a professional support team to resolve your concerns.
