As computers continue to advance, cybercriminals have developed more sophisticated virus software and disguised it as innocent games, with the goal of hijacking and controlling your PC. Refer to MiniTool and discuss the Winos4.0 malware hides in game issue.
Primary Understanding of Winos4.0
Winos4.0 is an advanced malicious framework that possesses a comprehensive range of features, a sturdy architecture, and the capacity to effectively control numerous online endpoints, facilitating subsequent actions. The framework was identified as being embedded in Windows-oriented gaming-related applications, especially in popular games and assistive tools, which makes its dissemination channels more concealed and harder to spot.
According to recent studies, this malware framework is an advanced variant of Gh0strat. Malicious Winos4.0 is capable of carrying out various remote operations and granting attackers extensive control over affected systems. This control goes beyond basic information theft and encompasses more complex data manipulation and system management functions, enabling attackers to conduct long-term surveillance without being detected.
The malware gains initial access to the target device by distributing game-related applications such as installation tools and performance enhancers. Once a user installs one of these applications, it downloads a seemingly innocuous BMP file from a remote server and extracts and activates the Winos4.0 DLL file. During this process, users are often oblivious to the potential threat they have introduced, as these files are frequently disguised as normal software components. What’s going on when Winos4.0 malware hides in game?
The first stage of the malicious game disguise creates an environment for the deployment of additional modules and establishes persistence on infected machines by creating registry keys or setting up scheduled tasks. This implies that even if users attempt to uninstall related applications, the malicious code can still persist and be reactivated, raising the difficulty of removal.
Also read: How to Uninstall Programs on Windows 11? 8 Ways Are Here!
Winos4.0 Comprehensive Functionality and Security Threats
In the second stage, the framework decrypts the hidden files to inject shellcode and loads the necessary modules to control the infected system. The key functions of this complex framework include clipboard monitoring, system information collection, and checks for antivirus software, encrypted wallet extensions, and other security applications.
These functions allow attackers to obtain sensitive information in real-time, such as passwords, account data, and personal identification information, thereby further expanding their scope of influence.
Furthermore, this complex framework also targets educational institutions, and the description in the document might suggest that it pays attention to the management functions of the campus.
Further analysis indicates that Winos4.0 communicates with the command-and-control server to download the encryption module. It acquires the server address from a specific registry key, allowing it to log in and maintain a connection. This connection not only enables the malware to receive instructions but also enables it to update itself dynamically to adapt to the constantly changing security environment. Therefore, even the latest version of the software may not be effective in detecting such threats.
The entire attack chain involves multiple encrypted data and a large number of command-and-control communications to complete the injection process. Therefore, in daily use, it is crucial to be vigilant about Winos4.0 malware hides in game and the sources of any new applications and only download software from verified and reputable channels. At the same time, enhancing cybersecurity awareness and improving preventive measures will help reduce the risk of encountering similar threats.
Backup Data to Protect Your PC
To take measures in advance against the time of need, you’d better create a backup for your Windows system. We highly recommend you try using MiniTool ShadowMaker which is a professional PC backup software. Other than system backup, file backup, disk cloning, and synchronization are all supportive.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
If the tool interests you, here’s a small operating instruction for you.
Step 1. Download and install MiniTool ShadowMaker. Then open it and click Keep Trial to enter its main interface.
Step 2. Head to Backup and the SOURCE module has defaulted to choose your entire operating system so you can directly click on DESTINATION to select a location for your backup file. Usually, it’s suggested you choose an external hard drive or a USB flash drive.
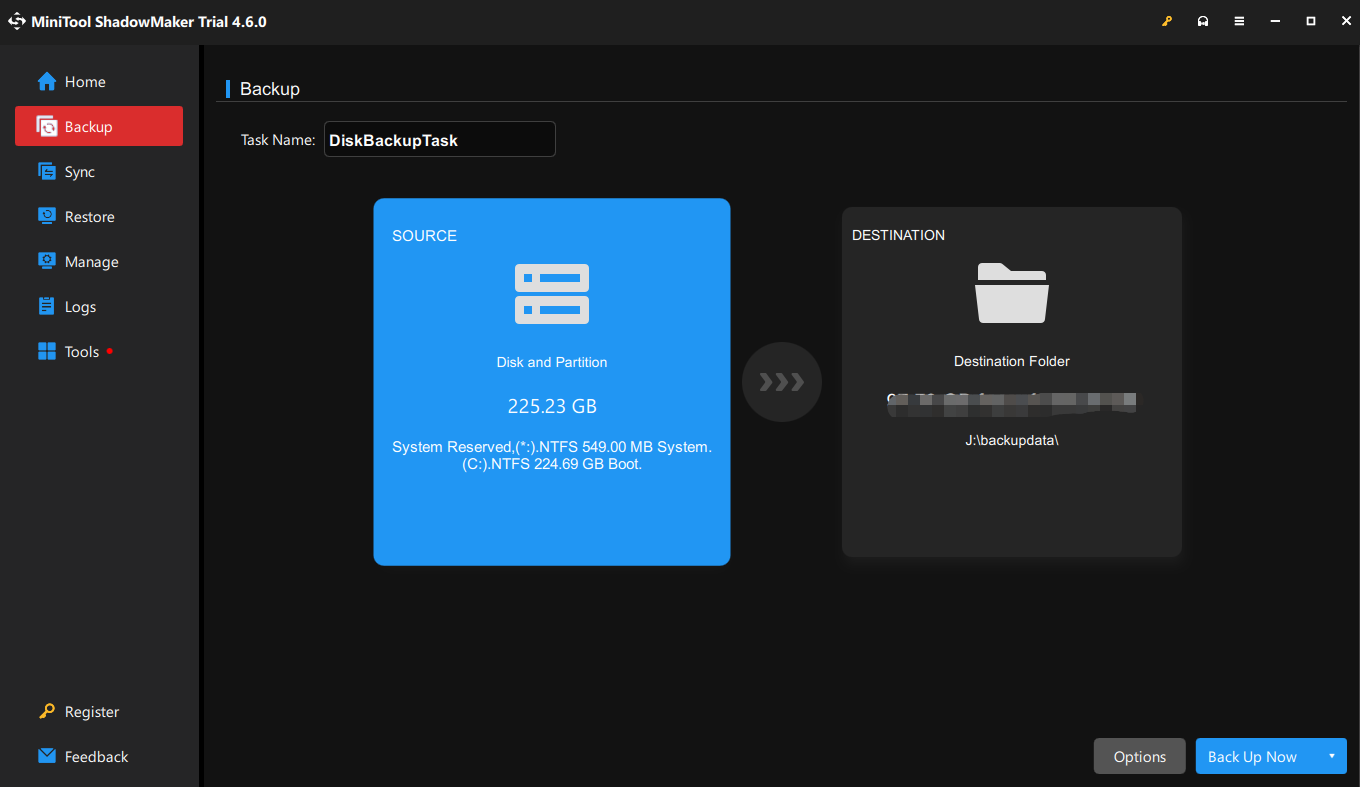
Step 3. After making your choice, click Back Up Now to start the work at once. The time of backup depends on your system.
Also see: How to Restore System Image from External Drive in Windows 11/10
Wrapping Things Up
In summary, this Winos4.0 malware hides in game situation can pose different levels of security risks to Windows users, and it is important to download software from reputable sources. In addition, regular backup is becoming increasingly important from today onwards.