Remote access is a convenient tech for workers at different locations. However, remote access scams come with malicious aims, such as stealing credential information on the computer, downloading malware secretly, or doing other operations. Fortunately, you have several approaches to check if someone is remotely accessing your computer. Keep reading and check your computer carefully.
Way 1. Check Recent Activities
Hackers remote access your computer with targets and operations will leave you traces. You can check the recent computer activities to tell if your computer is being accessed remotely.
- Check recently opened files/applications: Press Win + E to open Windows Explorer on your computer where you can browse the recently accessed files. Click on the Windows icon to see the recently opened apps.
- View browser history/downloads: Open browsers on your computer to check the browsing history and download list. You should ensure that all the visited websites and downloaded items are made by yourself.
- Check login events: Press Win + R to open the Run windows, then type eventvwr and press Enter to open Event Viewer. Head to Windows Logs > Security to check if there is someone attempting to log into your computer at an unusual time.
Way 2. View Programs via Task Manager
You can also check if someone is remotely accessing your computer by reviewing the programs in Task Manager. Programs may be remotely installed or accessed on your computer and run secretly. In this case, Task Manager is a good utility to check program status on your computer.
Press Ctrl + Shift + Esc to open Task Manager directly. Browse all the programs under the Processes tab. If there are any programs that are not installed or running by yourself, keep alert and check the application folder on your computer. You can seek help from professional computer services to remove suspicious software.
Way 3. Verify Windows Firewall Settings
Windows Firewall is a reliable and trustworthy tool that blocks unauthorized access to your computer effectively. Therefore, those remote access scammers may alter the Windows Firewall settings to ease their access.
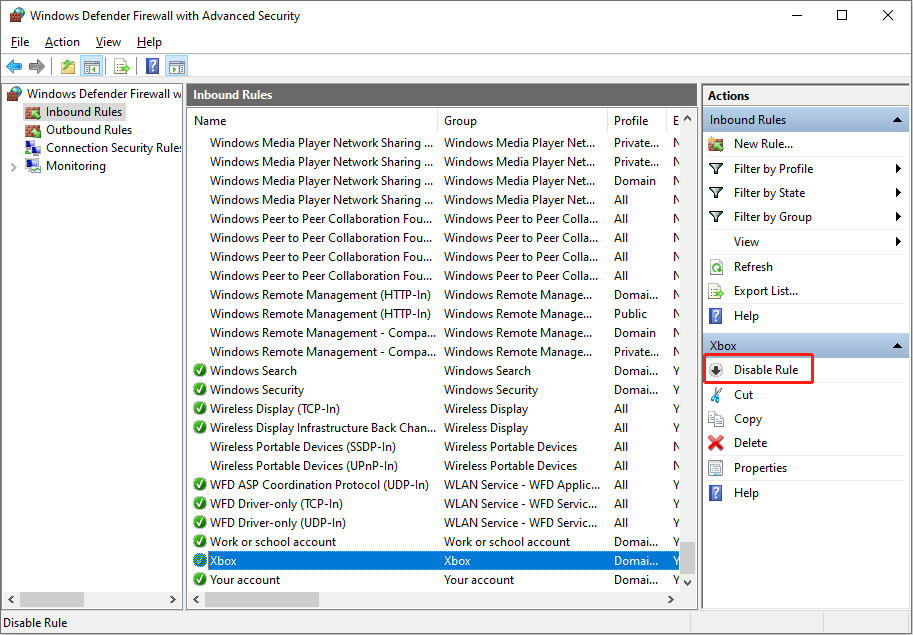
Type Windows Defender Firewall with Advanced Security into the Windows Search bar and hit Enter to open the window. You need to look through the inbound and outbound rules. If there are dubious rules, click on them and choose Disable Rule at the right sidebar. Before deleting the rule, you are advised to verify the authorization and legitimation of the rule.
Way 4. Perform a Virus Scan
An alert window may prompt up when the Windows utilities detect remote access to your computer. When you get such a message, perform a virus scan to avoid underlying viruses on the computer. You can use reliable third-party antivirus software or run a Windows-embedded utility, such as Windows Security.
Tips: Stop Someone from Accessing Your Computer Remotely
It is necessary to learn how to check if someone is remotely accessing your computer. You should also know tactics to stop someone from accessing your computer. Here are some suggestions:
- Disable remote connections: To reject all remote connections, you can disable the remote connection by opening System Properties and ticking the Don’t allow remote connections to this computer option. Afterward, click Apply > OK to save the change.
- Change passwords: If your computer has already been remotely accessed, you need to change all the passwords of your crucial accounts on another security device. This measure can prevent further threats.
- Use a VPN: A Virtual Private Network (VPN) can hide your actual location and encrypt your data, which is a secure network connection option. You can choose an authorized VPN, like MiniTool VPN, and get it from its official website.
- Back up files regularly: Some malicious software or ransomware may delete or lock your crucial files. If you have any backups, you can get back your data without paying for it. MiniTool ShadowMaker is a robust backup software that supports file backup, folder backup, partition backup, and disk backup. You can try the trial edition to use the backup features for free for 30 days.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Final Words
Cybercrimes occur in diverse forms. You should always keep alert in daily use and check if someone is remotely accessing your computer from time to time to ensure a secure environment for computer use.